About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 204 results network clear search
Tram Commute
Julia Kasmire | Published Thursday, February 13, 2020 | Last modified Monday, March 02, 2020A demonstration model showing how modellers can create a multi regional tram network with commuters, destinations and houses. The model offers options to create a random tram network made from modeller input or to load shapefiles for the Greater Manchester Metrolink.
The model uses NetLogo with gis, nw an csv extensions.
Consumats on a network
Marco Janssen | Published Tuesday, January 14, 2020 | Last modified Tuesday, May 30, 2023Consumer agents make choices which products to choose using the consumat approach. In this approach agents will make choices using deliberation, repetition, imitation or social comparison dependent on the level of need satisfaction and uncertainty.
The model is discussed in Introduction to Agent-Based Modeling by Marco Janssen. For more information see https://intro2abm.com/
A Bottom-Up Simulation on Competition and Displacement of Online Interpersonal Communication Platforms
great-sage-futao | Published Tuesday, December 31, 2019 | Last modified Tuesday, December 31, 2019This model aims to simulate Competition and Displacement of Online Interpersonal Communication Platforms process from a bottom-up angle. Individual interpersonal communication platform adoption and abandonment serve as the micro-foundation of the simulation model. The evolution mode of platform user online communication network determines how present platform users adjust their communication relationships as well as how new users join that network. This evolution mode together with innovations proposed by individual interpersonal communication platforms would also have impacts on the platform competition and displacement process and result by influencing individual platform adoption and abandonment behaviors. Three scenes were designed to simulate some common competition situations occurred in the past and current time, that two homogeneous interpersonal communication platforms competed with each other when this kind of platforms first came into the public eye, that a late entrant platform with a major innovation competed with the leading incumbent platform during the following days, as well as that both the leading incumbent and the late entrant continued to propose many small innovations to compete in recent days, respectively.
Initial parameters are as follows: n(Nmax in the paper), denotes the final node number of the online communication network node. mi (m in the paper), denotes the initial degree of those initial network nodes and new added nodes. pc(Pc in the paper), denotes the proportion of links to be removed and added in each epoch. pst(Pv in the paper), denotes the proportion of nodes with a viscosity to some platforms. comeintime(Ti in the paper), denotes the epoch when Platform 2 joins the market. pit(Pi in the paper), denotes the proportion of nodes adopting Platform 2 immediately at epoch comeintime(Ti). ct(Ct in the paper), denotes the Innovation Effective Period length. In Scene 2, There is only one major platform proposed by Platform 2, and ct describes that length. However, in Scene 3, Platform 2 and 1 will propose innovations alternately. And so, we set ct=10000 in simulation program, and every jtt epochs, we alter the innovation proposer from one platform to the other. Hence in this scene, jtt actually denotes the Innovation Effective Period length instead of ct.
Cultural Evolution of Sustainable Behaviours: Landscape of Affordances Model
Nikita Strelkovskii Roope Oskari Kaaronen | Published Wednesday, December 04, 2019 | Last modified Wednesday, December 04, 2019This NetLogo model illustrates the cultural evolution of pro-environmental behaviour patterns. It illustrates how collective behaviour patterns evolve from interactions between agents and agents (in a social network) as well as agents and the affordances (action opportunities provided by the environment) within a niche. More specifically, the cultural evolution of behaviour patterns is understood in this model as a product of:
- The landscape of affordances provided by the material environment,
- Individual learning and habituation,
- Social learning and network structure,
- Personal states (such as habits and attitudes), and
…
A network agent-based model of ethnocentrism and intergroup cooperation
Ross Gore | Published Sunday, October 27, 2019We present a network agent-based model of ethnocentrism and intergroup cooperation in which agents from two groups (majority and minority) change their communality (feeling of group solidarity), cooperation strategy and social ties, depending on a barrier of “likeness” (affinity). Our purpose was to study the model’s capability for describing how the mechanisms of preexisting markers (or “tags”) that can work as cues for inducing in-group bias, imitation, and reaction to non-cooperating agents, lead to ethnocentrism or intergroup cooperation and influence the formation of the network of mixed ties between agents of different groups. We explored the model’s behavior via four experiments in which we studied the combined effects of “likeness,” relative size of the minority group, degree of connectivity of the social network, game difficulty (strength) and relative frequencies of strategy revision and structural adaptation. The parameters that have a stronger influence on the emerging dominant strategies and the formation of mixed ties in the social network are the group-tag barrier, the frequency with which agents react to adverse partners, and the game difficulty. The relative size of the minority group also plays a role in increasing the percentage of mixed ties in the social network. This is consistent with the intergroup ties being dependent on the “arena” of contact (with progressively stronger barriers from e.g. workmates to close relatives), and with measures that hinder intergroup contact also hindering mutual cooperation.
NetLogo HIV spread model
Wouter Vermeer | Published Friday, October 25, 2019This model describes the tranmission of HIV by means of unprotected anal intercourse in a population of men-who-have-sex-with-men.
The model is parameterized based on field data from a cohort study conducted in Atlanta Georgia.
Waste separation in small-world networks
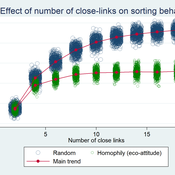
František Kalvas Michaela Kudrnáčová | Published Monday, September 30, 2019The model answers the question how homophily and number of close-links in small-world network influences behavior of consumats. The results show that the more close-links the more probable the consumat follows the major behavior, but homophilly blocks the major behavior and supports survival of the minor behavior.
Homophily as a process generating social networks: insights from Social Distance Attachment model
Szymon Talaga Andrzej Nowak | Published Tuesday, September 17, 2019This is code repository for the paper “Homophily as a process generating social networks: insights from Social Distance Attachment model”.
It provides all information, code and data necessary to replicate all the simulations and analyses presented in the paper.
This document contains the overall instruction as well as description of the content of the repository.
Details regarding particular stages are documented within source files as comments.
A double-layer network and the contagion mechanism of China’s financial systemic risk
zou | Published Tuesday, August 13, 2019We establish a double-layer network for China’s financial system, consisting of an interbank lending network and a cross-shareholding network. The loss of diffusion in an interbank lending channel independently, a cross-shareholding channel independently and a double-layer contagion channel after one of the financial institutions goes bankrupt with an initial shock are simulated to explore the nonlinear evolution mechanism of financial risk and impact factors of financial systemic risk in China.
An agent-based artificial stock with a dynamic investor network
Matthew Oldham | Published Tuesday, June 25, 2019The model is an agent-based artificial stock market where investors connect in a dynamic network. The network is dynamic in the sense that the investors, at specified intervals, decide whether to keep their current adviser (those investors they receive trading advise from). The investors also gain information from a private source and share public information about the risky asset. Investors have different tendencies to follow the different information sources, consider differing amounts of history, and have different thresholds for investing.
Displaying 10 of 204 results network clear search