About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 142 results #Networks clear search
City Sandbox
Javier Sandoval | Published Thursday, January 09, 2020This model grows land use patterns that emerge as a result of land-use compatibilities stablished in urban development plans, land topography, and street networks. It contains urban brushes to paint streets and land uses as a way to learn about urban pattern emergence through free experimentation.
Managing networked landscapes: conservation in fragmented, regionally connected world
Jacopo A. Baggio Michael Schoon Sechindra Vallury | Published Monday, December 09, 2019Exploring how learning and social-ecological networks influence management choice set and their ability to increase the likelihood of species coexistence (i.e. biodiversity) on a fragmented landscape controlled by different managers.
An agent-based model to simulate meat consumption behaviour of consumers in Britain
Andrea Scalco | Published Friday, October 18, 2019The current rate of production and consumption of meat poses a problem both to peoples’ health and to the environment. This work aims to develop a simulation of peoples’ meat consumption behaviour in Britain using agent-based modelling. The agents represent individual consumers. The key variables that characterise agents include sex, age, monthly income, perception of the living cost, and concerns about the impact of meat on the environment, health, and animal welfare. A process of peer influence is modelled with respect to the agents’ concerns. Influence spreads across two eating networks (i.e. co-workers and household members) depending on the time of day, day of the week, and agents’ employment status. Data from a representative sample of British consumers is used to empirically ground the model. Different experiments are run simulating interventions of application of social marketing campaigns and a rise in price of meat. The main outcome is the average weekly consumption of meat per consumer. A secondary outcome is the likelihood of eating meat.
Waste separation in small-world networks
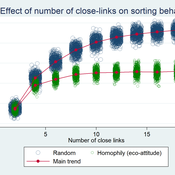
František Kalvas Michaela Kudrnáčová | Published Monday, September 30, 2019The model answers the question how homophily and number of close-links in small-world network influences behavior of consumats. The results show that the more close-links the more probable the consumat follows the major behavior, but homophilly blocks the major behavior and supports survival of the minor behavior.
Homophily as a process generating social networks: insights from Social Distance Attachment model
Szymon Talaga Andrzej Nowak | Published Tuesday, September 17, 2019This is code repository for the paper “Homophily as a process generating social networks: insights from Social Distance Attachment model”.
It provides all information, code and data necessary to replicate all the simulations and analyses presented in the paper.
This document contains the overall instruction as well as description of the content of the repository.
Details regarding particular stages are documented within source files as comments.
NarcoLogic
Nicholas Magliocca | Published Thursday, August 29, 2019Investigate spatial adaptive behaviors of narco-trafficking networks in response to various counterdrug interdiction strategies within the cocaine transit zone of Central America and associated maritime areas. Through the novel application of the ‘complex adaptive systems’ paradigm, we implement a potentially transformative coupled agent-based and interdiction optimization modeling approach to compellingly demonstrate: (a) how current efforts to disrupt narco-trafficking networks are in fact making them more widespread, resilient, and economically powerful; (b) the potential for alternative interdiction approaches to weaken and contain traffickers.
Relational integration in schools through seating assignments
Károly Takács Marta Rado | Published Thursday, July 18, 2019We model interpersonal dynamics and study behavior in the classroom in the hypothetical case of a single teacher who defines students’ seating arrangements. The model incorporates the mechanisms of peer influence on study behavior, on attitude formation, and homophilous selection in order to depict the interrelated dynamics of networks, behavior, and attitudes. We compare various seating arrangement scenarios and observe how GPA distribution and level of prejudice changes over time.
MERCURY extension: population
Tom Brughmans | Published Thursday, May 23, 2019This model is an extended version of the original MERCURY model (https://www.comses.net/codebases/4347/releases/1.1.0/ ) . It allows for experiments to be performed in which empirically informed population sizes of sites are included, that allow for the scaling of the number of tableware traders with the population of settlements, and for hypothesised production centres of four tablewares to be used in experiments.
Experiments performed with this population extension and substantive interpretations derived from them are published in:
Hanson, J.W. & T. Brughmans. In press. Settlement scale and economic networks in the Roman Empire, in T. Brughmans & A.I. Wilson (ed.) Simulating Roman Economies. Theories, Methods and Computational Models. Oxford: Oxford University Press.
…
LaMEStModel
Ruth Meyer | Published Friday, October 12, 2018The Labour Markets and Ethnic Segmentation (LaMESt) Model is a model of a simplified labour market, where only jobs of the lowest skill level are considered. Immigrants of two different ethnicities (“Latino”, “Asian”) compete with a majority (“White”) and minority (“Black”) native population for these jobs. The model’s purpose is to investigate the effect of ethnically homogeneous social networks on the emergence of ethnic segmentation in such a labour market. It is inspired by Waldinger & Lichter’s study of immigration and the social organisation of labour in 1990’s Los Angeles.
Peer reviewed MigrAgent
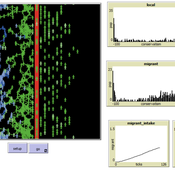
Wander Jager Rocco Paolillo | Published Friday, October 05, 2018 | Last modified Wednesday, November 28, 2018MigrAgent simulates migration flows of a population from a home country to a host country and mutual adaptation of a migrant and local population post-migration. Agents accept interactions in intercultural networks depending on their degree of conservatism. Conservatism is a group-level parameter normally distributed within each ethnic group. Individual conservatism changes as function of reciprocity of interaction in intergroup experiences of acceptance or rejection.
The aim of MigrAgent is to unfold different outcomes of integration, assimilation, separation and marginalization in terms of networks as effect of different degrees of conservatism in each group and speed of migration flows.
Displaying 10 of 142 results #Networks clear search