About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 933 results for "Ibo van de Poel" clear search
Two agent-based models of cooperation in dynamic groups and fixed social networks
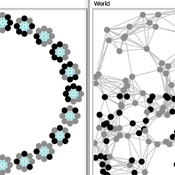
Carlos A. de Matos Fernandes | Published Thursday, January 20, 2022Both models simulate n-person prisoner dilemma in groups (left figure) where agents decide to C/D – using a stochastic threshold algorithm with reinforcement learning components. We model fixed (single group ABM) and dynamic groups (bad-barrels ABM). The purpose of the bad-barrels model is to assess the impact of information during meritocratic matching. In the bad-barrels model, we incorporated a multidimensional structure in which agents are also embedded in a social network (2-person PD). We modeled a random and homophilous network via a random spatial graph algorithm (right figure).
Opinion Leaders' Role in Innovation Diffusion
Peter Van Eck | Published Wednesday, March 10, 2010 | Last modified Saturday, April 27, 2013This model is used to investigate the role of opinion leader. More specifically: the influence of ‘innovative behavior’, ‘weigth of normative influence’, ‘better product judgment’, ‘number of opinion
CPNorm
Ruth Meyer | Published Sunday, June 04, 2017 | Last modified Tuesday, June 13, 2017CPNorm is a model of a community of harvesters using a common pool resource where adhering to the optimal extraction level has become a social norm. The model can be used to explore the robustness of norm-driven cooperation in the commons.
SMILI: Small-scale fisheries Institutions and Local Interactions
Emilie Lindkvist Maja Schlüter Xavier Basurto | Published Thursday, March 09, 2017The model represents an archetypical fishery in a co-evolutionary social-ecological environment, capturing different dimensions of trust between fishers and fish buyers for the establishment and persistence of self-governance arrangements.
MCR Model
Davide Secchi Nuno R Barros De Oliveira | Published Friday, July 22, 2016 | Last modified Saturday, January 23, 2021The aim of the model is to define when researcher’s assumptions of dependence or independence of cases in multiple case study research affect the results — hence, the understanding of these cases.
Physical activity promotion and the United Nations Sustainable Development Goals
Leandro Garcia Ivana Stankov Rahul Goel | Published Tuesday, March 01, 2022This model was created to investigate the potential impacts of large-scale recreational and transport-related physical activity promotion strategies on six United Nations Sustainable Development Goals (SDGs) related outcomes—road traffic deaths (SDG 3), transportation mode share (SDG 9), convenient access to public transport, levels of fine particulate matter, and access to public open spaces (SDG 11), and levels of carbon dioxide emissions (SDG 13)—in three cities designed as abstract representations of common city types in high-, middle-, and low-income countries.
Peninsula_Iberica 1.0
Carolina Cucart-Mora Sergi Lozano Javier Fernández-López De Pablo | Published Friday, November 04, 2016 | Last modified Monday, November 27, 2017This model was build to explore the bio-cultural interaction between AMH and Neanderthals during the Middle to Upper Paleolithic Transition in the Iberian Peninsula
Peer reviewed Ants Digging Networks
Elske van der Vaart | Published Friday, September 14, 2018This is a NetLogo version of Buhl et al.’s (2005) model of self-organised digging activity in ant colonies. It was built for a master’s course on self-organisation and its intended use is still educational. The ants’ behavior can easily be changed by toggling switches on the interface, or, for more advanced students, there is R code included allowing the model to be run and analysed through RNetLogo.
Non-attentional visual information transmission in groups under predation
J. Fransje Weerden, van | Published Wednesday, March 25, 2020Our aim is to show effects of group living when only low-level cognition is assumed, such as pattern recognition needed for normal functioning, without assuming individuals have knowledge about others around them or warn them actively.
The model is of a group of vigilant foragers staying within a patch, under attack by a predator. The foragers use attentional scanning for predator detection, and flee after detection. This fleeing action constitutes a visual cue to danger, and can be received non-attentionally by others if it occurs within their limited visual field. The focus of this model is on the effectiveness of this non-attentional visual information reception.
A blind angle obstructing cue reception caused by behaviour can exist in front, morphology causes a blind angle in the back. These limitations are represented by two visual field shapes. The scan for predators is all-around, with distance-dependent detection; reception of flight cues is limited by visual field shape.
Initial parameters for instance: group sizes, movement, vision characteristics for predator detection and for cue reception. Captures (failure), number of times the information reached all individuals at the same time (All-fled, success), and several other effects of the visual settings are recorded.
Peer reviewed Casting: A Bio-Inspired Method for Restructuring Machine Learning Ensembles
Colin Lynch Bryan Daniels | Published Thursday, September 18, 2025The wisdom of the crowd refers to the phenomenon in which a group of individuals, each making independent decisions, can collectively arrive at highly accurate solutions—often more accurate than any individual within the group. This principle relies heavily on independence: if individual opinions are unbiased and uncorrelated, their errors tend to cancel out when averaged, reducing overall bias. However, in real-world social networks, individuals are often influenced by their neighbors, introducing correlations between decisions. Such social influence can amplify biases, disrupting the benefits of independent voting. This trade-off between independence and interdependence has striking parallels to ensemble learning methods in machine learning. Bagging (bootstrap aggregating) improves classification performance by combining independently trained weak learners, reducing bias. Boosting, on the other hand, explicitly introduces sequential dependence among learners, where each learner focuses on correcting the errors of its predecessors. This process can reinforce biases present in the data even if it reduces variance. Here, we introduce a new meta-algorithm, casting, which captures this biological and computational trade-off. Casting forms partially connected groups (“castes”) of weak learners that are internally linked through boosting, while the castes themselves remain independent and are aggregated using bagging. This creates a continuum between full independence (i.e., bagging) and full dependence (i.e., boosting). This method allows for the testing of model capabilities across values of the hyperparameter which controls connectedness. We specifically investigate classification tasks, but the method can be used for regression tasks as well. Ultimately, casting can provide insights for how real systems contend with classification problems.
Displaying 10 of 933 results for "Ibo van de Poel" clear search