About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 1113 results for "Bin-Tzong Chi" clear search
This is an agent-based model that simulates the structural evolution in food supply chain.
Model supporting the serious game RÁC
Patrick Taillandier Alexis Drogoul Léo Biré | Published Thursday, January 25, 2024This model is supporting the serious game RÁC (“waste” in Vietnamese), dedicated to foster discussion about solid waste management in a Vietnamese commune in the Bắc Hưng Hải irrigation system.
The model is replicating waste circulation and environmental impact in four fictive villages. During the game, the players take actions and see how their decisions have an impact on the model.
This model was implemented using the GAMA platform, using gaml language.
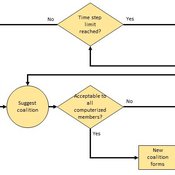
Heuristic Algorithm for Generating Strategic Coalition Structures
Andrew Collins Daniele Vernon-Bido | Published Monday, October 12, 2020The purpose of the model is to generate coalition structures of different glove games, using a specially designed algorithm. The coalition structures can be are later analyzed by comparing them to core partitions of the game used. Core partitions are coalition structures where no subset of players has an incentive to form a new coalition.
The algorithm used in this model is an advancement of the algorithm found in Collins & Frydenlund (2018). It was used used to generate the results in Vernon-Bido & Collins (2021).
Agent-Based Model of Social Care with Kinship Networks
Umberto Gostoli Eric Silverman | Published Thursday, October 14, 2021The purpose of this model is the simulation of social care provision in the UK, in which individual agents can decide to provide informal care, or pay for private care, for their loved ones. Agents base these decisions on factors including their own health, employment status, financial resources, relationship to the individual in need and geographical location. The model simulates care provision as a negotiation process conducted between agents across their kinship networks, with agents with stronger familial relationships to the recipient being more likely to attempt to allocate time to care provision. The model also simulates demographic change, the impact of socioeconomic status, and allows agents to relocate and change jobs or reduce working hours in order to provide care.
Despite the relative lack of empirical data in this model, the model is able to reproduce plausible patterns of social care provision. The inclusion of detailed economic and behavioural mechanisms allows this model to serve as a useful policy development tool; complex behavioural interventions can be implemented in simulation and tested on a virtual population before applying them in real-world contexts.
A basic macroeconomic agent-based model for analyzing monetary regime shifts
Oliver Reinhardt Florian Peters Doris Neuberger Adelinde Uhrmacher | Published Tuesday, May 03, 2022In macroeconomics, an emerging discussion of alternative monetary systems addresses the dimensions of systemic risk in advanced financial systems. Monetary regime changes with the aim of achieving a more sustainable financial system have already been discussed in several European parliaments and were the subject of a referendum in Switzerland. However, their effectiveness and efficacy concerning macro-financial stability are not well-known. This paper introduces a macroeconomic agent-based model (MABM) in a novel simulation environment to simulate the current monetary system, which may serve as a basis to implement and analyze monetary regime shifts. In this context, the monetary system affects the lending potential of banks and might impact the dynamics of financial crises. MABMs are predestined to replicate emergent financial crisis dynamics, analyze institutional changes within a financial system, and thus measure macro-financial stability. The used simulation environment makes the model more accessible and facilitates exploring the impact of different hypotheses and mechanisms in a less complex way. The model replicates a wide range of stylized economic facts, including simplifying assumptions to reduce model complexity.
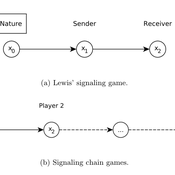
Lewis' Signaling Chains
Giorgio Gosti | Published Wednesday, January 14, 2015 | Last modified Friday, April 03, 2015Signaling chains are a special case of Lewis’ signaling games on networks. In a signaling chain, a sender tries to send a single unit of information to a receiver through a chain of players that do not share a common signaling system.
Pedestrian model
Gudrun Wallentin Dana Kaziyeva Martin Loidl Petra Stutz | Published Monday, August 07, 2023The model generates disaggregated traffic flows of pedestrians, simulating their daily mobility behaviour represented as probabilistic rules. Various parameters of physical infrastructure and travel behaviour can be altered and tested. This allows predicting potential shifts in traffic dynamics in a simulated setting. Moreover, assumptions in decision-making processes are general for mid-sized cities and can be applied to similar areas.
Together with the model files, there is the ODD protocol with the detailed description of model’s structure. Check the associated publication for results and evaluation of the model.
Installation
Download GAMA-platform (GAMA1.8.2 with JDK version) from https://gama-platform.github.io/. The platform requires a minimum of 4 GB of RAM.
…
Peer reviewed Historical Letters
Bernardo Buarque Malte Vogl Jascha Merijn Schmitz Aleksandra Kaye | Published Thursday, May 16, 2024 | Last modified Friday, May 24, 2024A letter sending model with historically informed initial positions to reconstruct communication and archiving processes in the Republic of Letters, the 15th to 17th century form of scholarship.
The model is aimed at historians, willing to formalize historical assumptions about the letter sending process itself and allows in principle to set heterogeneous social roles, e.g. to evaluate the role of gender or social status in the formation of letter exchange networks. The model furthermore includes a pruning process to simulate the loss of letters to critically asses the role of biases e.g. in relation to gender, geographical regions, or power structures, in the creation of empirical letter archives.
Each agent has an initial random topic vector, expressed as a RGB value. The initial positions of the agents are based on a weighted random draw based on data from [2]. In each step, agents generate two neighbourhoods for sending letters and potential targets to move towards. The probability to send letters is a self-reinforcing process. After each sending the internal topic of the receiver is updated as a movement in abstract space by a random amount towards the letters topic.
…
MERCURY extension: transport-cost
Tom Brughmans | Published Monday, July 23, 2018This is extended version of the MERCRUY model (Brughmans 2015) incorporates a ‘transport-cost’ variable, and is otherwise unchanged. This extended model is described in this publication: Brughmans, T., 2019. Evaluating the potential of computational modelling for informing debates on Roman economic integration, in: Verboven, K., Poblome, J. (Eds.), Structural Determinants in the Roman World.
Brughmans, T., 2015. MERCURY: an ABM of tableware trade in the Roman East. CoMSES Comput. Model Libr. URL https://www.comses.net/codebases/4347/releases/1.1.0/
Ornstein-Uhlenbeck Pandemic package
Peter Cotton | Published Friday, April 24, 2020 | Last modified Friday, May 08, 2020Pandemic (pip install pandemic)
An agent model in which commuting, compliance, testing and contagion parameters drive infection in a population of thousands of millions. Agents follow Ornstein-Uhlenbeck processes in the plane and collisions drive transmission. Results are stored at SwarmPrediction.com for further analysis, and can be retrieved by anyone.
This is a very simple simulation that in a special case can be shown to be approximated by a compartmental model with time varying infection rate.
Displaying 10 of 1113 results for "Bin-Tzong Chi" clear search