About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 966 results for "Dave van Wees" clear search
An agent-based model to study the effects of urban sprawl on bird distribution
Yun Ouyang | Published Tuesday, December 16, 2008 | Last modified Saturday, April 27, 2013This model was programmed for a class project, which studied the effects of urban sprawl on bird distribution. For the urban sprawl part of the model, we started from the model in (udhira, H. S., 200
An agent based simulation and data mining framework for scenario analysis of technology products
Moeed Haghnevis | Published Monday, December 13, 2010 | Last modified Saturday, April 27, 2013The objective of this study is to create a framework to simulate and analyze the effect of multiple business scenarios on the adoption behavior of a group of technology products.
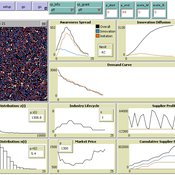
(Policy induced) Diffusion of Innovations - An integrated demand-supply Model based on Cournot Competition
Martin Rixin | Published Monday, August 29, 2011 | Last modified Saturday, April 27, 2013Objective is to simulate policy interventions in an integrated demand-supply model. The underlying demand function links both sides. Diffusion proceeds if interactions distribute awareness (Epidemic effect) and rivalry reduces the market price (Probit effect). Endogeneity is given due to the fact that consumer awareness as well as their willingness-to-pay drives supply-side rivalry. Firm´s entry and exit decisions as well as quantity and price settings are driven by Cournot competition.
Managing Connectivity: insights from modelling species interactions accross multiple scales in an idealized landscape
Marco Janssen Michael Schoon Jacopo A. Baggio Kehinde Salau | Published Monday, October 01, 2012 | Last modified Monday, January 20, 2014The model objective’s is to explore the management choice set to uncover which subsets of strategies are most effective at maximizing species coexistence on a fragmented landscape.
Parental choices, children's skills, and skill inequality: An agent-based model implemented in Python
Andrés Cardona | Published Thursday, October 30, 2014The model explores the emergence of inequality in cognitive and socio-emotional skills at the societal level within and across generations that results from differences in parental investment behavior during childhood and adolescence.
Long Term Impacts of Bank Behavior on Financial Stability An Agent Based Modeling Approach
Ilker Arslan | Published Tuesday, October 13, 2015 | Last modified Monday, April 08, 2019This model simulates a bank - firm credit network.
AMBAWA, an Agent-based Model of Biomass flows in Agropastoral areas of West Africa
Christophe Le Page Tidiane Diarisso Nadine Andrieu Marc Corbeels François Bousquet Pablo Tittonell David Berre | Published Monday, November 23, 2015 | Last modified Sunday, April 12, 2020AMBAWA simulates the flows of biomass between crop and livestock systems at the field, farm, and village scales in order to showcase innovating management practices of soil fertility in West Africa.
An agent-based simulation model simulating the problem solving process of tournament-based crowdsourcing
wiseyanjie | Published Friday, May 04, 2018 | Last modified Friday, July 06, 2018A series of studies show the applicability of the NK model in the crowdsourcing research, but it also exposes a problem that the application of the NK model is not tightly integrated with crowdsourcing process, which leads to lack of a basic crowdsourcing simulation model. Accordingly, by introducing interaction relationship among task decisions to define three tasks of different structure: local task, small-world task and random task, and introducing bounded rationality and its two dimensions are taken into account: bounded rationality level that used to distinguish industry types and bounded rationality bias that used to differentiate professional users and ordinary users, an agent-based model that simulates the problem-solving process of tournament-based crowdsourcing is constructed by combining the NK fitness landscapes and the crowdsourcing framework of “Task-Crowd-Process-Evaluation”.
The Regional Security Game: An Agent-based, Evolutionary Model of Strategic Evolution and Stability
Anthony Skews | Published Saturday, June 09, 2018The Regional Security Game is a iterated public goods game with punishement based on based on life sciences work by Boyd et al. (2003 ) and Hintze & Adami (2015 ), with modifications appropriate for an international relations setting. The game models a closed regional system in which states compete over the distribution of common security benefits. Drawing on recent work applying cultural evolutionary paradigms in the social sciences, states learn through imitation of successful strategies rather than making instrumentally rational choices. The model includes the option to fit empirical data to the model, with two case studies included: Europe in 1933 on the verge of war and south-east Asia in 2013.
An agent-based simulation model simulating the problem solving process of tournament-based crowdsourcing
wiseyanjie | Published Friday, July 06, 2018A series of studies show the applicability of the NK model in the crowdsourcing research, but it also exposes a problem that the application of the NK model is not tightly integrated with crowdsourcing process, which leads to lack of a basic crowdsourcing simulation model. Accordingly, by introducing interaction relationship among task decisions to define three tasks of different structure: local task, small-world task and random task, and introducing bounded rationality and its two dimensions are taken into account: bounded rationality level that used to distinguish industry types and bounded rationality bias that used to differentiate professional users and ordinary users, an agent-based model that simulates the problem-solving process of tournament-based crowdsourcing is constructed by combining the NK fitness landscapes and the crowdsourcing framework of “Task-Crowd-Process-Evaluation”.
Displaying 10 of 966 results for "Dave van Wees" clear search