About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 334 results for "Chelsea E Hunter" clear search
Adoption of conservation practices
Irem Daloglu | Published Monday, October 21, 2013This model is designed to investigate the impact of alternative policy approaches and changing land tenure dynamics on farmer adoption of conservation practices intended to increase the water quality.
Peer reviewed Routes & Rumours 0.1.1
Jakub Bijak Martin Hinsch Oliver Reinhardt | Published Tuesday, July 12, 2022Routes & Rumours is an agent-based model of (forced) human migration. We model the formation of migration routes under the assumption that migrants have limited geographical knowledge concerning the transit area and rely to a large degree on information obtained from other migrants.
A Model to Unravel the Complexity of Rural Food Security
Stefano Balbi Samantha Dobbie | Published Monday, August 22, 2016 | Last modified Sunday, December 02, 2018An ABM to simulate the behaviour of households within a village and observe the emerging properties of the system in terms of food security. The model quantifies food availability, access, utilisation and stability.
An integrated socio-economic Agent-Based Modeling framework towards assessing farmers’ decision making under water scarcity and varying utility function
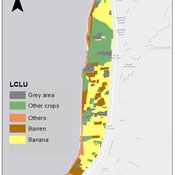
Ghinwa Harik | Published Tuesday, September 13, 2022 | Last modified Wednesday, November 23, 2022A spatio-temporal Agent Based Modeling (ABM) framework is developed to probabilistically predict farmers’ decisions in the context of climate-induced water scarcity under varying utility optimization functions. The proposed framework forecasts farmers’ behavior assuming varying utility functions. The framework allows decision makers to forecast the behavior of farmers through a user-friendly platform with clear output visualization. The functionality of the proposed ABM is illustrated in an agriculturally dominated plain along the Eastern Mediterranean coastline.
Study area GIS data available upon request to gxh00@mail.aub.edu
Protein 2.0: An Agent-Based Model for Simulating Norway’s Protein Sector Under Carbon Pricing and the Emergence of Cultivated Proteins
Gary Polhill Nick Roxburgh Rob J.F. Burton Klaus Mittenzwei | Published Thursday, May 08, 2025Protein 2.0 is a systems model of the Norwegian protein sector designed to explore the potential impacts of carbon taxation and the emergence of cultivated meat and dairy technologies. The model simulates production, pricing, and consumption dynamics across conventional and cultivated protein sources, accounting for emissions intensity, technological learning, economies of scale, and agent behaviour. It assesses how carbon pricing could alter the competitiveness of conventional beef, lamb, pork, chicken, milk, and egg production relative to emerging cultivated alternatives, and evaluates the implications for domestic production, emissions, and food system resilience. The model provides a flexible platform for exploring policy scenarios and transition pathways in protein supply. Further details can be found in the associated publication.
Simulating the evolution of the human family
Paul Smaldino | Published Wednesday, November 29, 2017The (cultural) evolution of cooperative breeding in harsh environments.
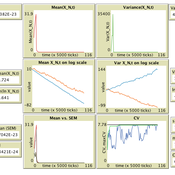
Population size limits the coefficient of variation in continuous traits affected by proportional copying error
Luke Premo | Published Thursday, June 18, 2020This version of the accumulated copying error (ACE) model is designed to address the following research question: how does finite population size (N) affect the coefficient of variation (CV) of a continuous cultural trait under the assumptions that the only source of copying error is visual perception error and that the continuous trait can take any positive value (i.e., it has no upper bound)? The model allows one to address this question while assuming the continuous trait is transmitted via vertical transmission, unbiased transmission, prestige biased transmission, mean conformist transmission, or median conformist transmission. By varying the parameter, p, one can also investigate the effect of population size under a mix of vertical and non-vertical transmission, whereby on average (1-p)N individuals learn via vertical transmission and pN individuals learn via either unbiased transmission, prestige biased transmission, mean conformist transmission, or median conformist transmission.
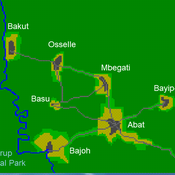
A stylized scale model to codesign with villagers an agent-based model of bushmeat hunting in the periphery of Korup National Park (Cameroon)
FOUR SEASONS
Lars G Spang | Published Tuesday, March 28, 2017Butterflies (turtles) goes through metamorphism and moves to corresponding patches each season of the year. The number of years and seasons are monitored.
Exploring Transitions towards Sustainable Construction
Jesus Rosales-Carreon César García-Díaz | Published Wednesday, October 30, 2013 | Last modified Saturday, January 31, 2015This model illustrates actor interaction in the construction sector, according to information gathered in NL. It offers a simple frame to represent diverse interests, interdependencies and effects on the number of built sustainable houses.
Displaying 10 of 334 results for "Chelsea E Hunter" clear search