About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 1188 results for "Ian M Hamilton" clear search
Livestock drought insurance model
Birgit Müller Felix John Jürgen Groeneveld Karin Frank Russell Toth | Published Tuesday, December 19, 2017 | Last modified Saturday, April 14, 2018The model analyzes the economic and ecological effects of a provision of livestock drought insurance for dryland pastoralists. More precisely, it yields qualitative insights into how long-term herd and pasture dynamics change through insurance.
Peer reviewed Modelling Agricultural Innovations as a Social-Ecological Phenomenon
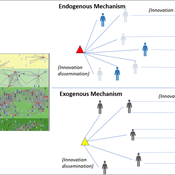
Maja Schlüter Udita Sanga | Published Thursday, November 17, 2022The goal of the AG-Innovation agent-based model is to explore and compare the effects of two alternative mechanisms of innovation development and diffusion (exogenous, linear and endogenous, non-linear) on emergent properties of food and income distribution and adoption rates of different innovations. The model also assesses the range of conditions under which these two alternative mechanisms would be effective in improving food security and income inequality outcomes. Our modelling questions were: i) How do cross-scalar social-ecological interactions within agricultural innovation systems affect system outcomes of food security and income inequality? ii) Do foreign aid-driven exogenous innovation perpetuate income inequality and food insecurity and if so, under which conditions? iii) Do community-driven endogenous innovations improve food security and income inequality and if so, under which conditions? The Ag-Innovation model is intended to serve as a thinking tool for for the development and testing of hypotheses, generating an understanding of the behavior of agricultural innovation systems, and identifying conditions under which alternated innovation mechanisms would improve food security and income inequality outcomes.
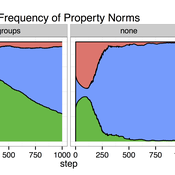
Cultural Group Selection of Sustainable Institutions
Timothy Waring Paul Smaldino Sandra H Goff | Published Wednesday, June 10, 2015 | Last modified Tuesday, August 04, 2015We develop a spatial, evolutionary model of the endogenous formation and dissolution of groups using a renewable common pool resource. We use this foundation to measure the evolutionary pressures at different organizational levels.
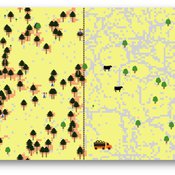
TRUE GRASP (Tree Recruitment Under Exotic GRAsses in a Savanna-Pineland)
is a socio-ecological agent-based model (ABM) and role playing game (RPG) for farmers and other stakeholders involved in rural landscape planning.
The purpose of this model is to allow actors to explore the individual and combined effects - as well as tradeoffs - of three methods of controlling exotic grasses in pine savannas: fire, weeding, and grazing cattle.
Design of TRUE GRASP is based on 3 years of socio-ecological fieldwork in a human-induced pine savanna in La Sepultura Biosphere Reserve (SBR) in the Mexican state of Chiapas. In this savanna, farmers harvest resin from Pinus oocarpa, which is used to produce turpentine and other products. However, long term persistence of this activity is jeopardized by low tree recruitment due to exotic tall grass cover in the forest understory (see Braasch et al., 2017). The TRUE GRASP model provides the user with different management strategies for controlling exotic grass cover and avoiding possible regime shifts, which in the case of the SBR would jeopardize resin harvesting.
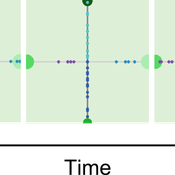
Feedback Loop Example: Forest Resource Transport
James Millington | Published Friday, December 21, 2012 | Last modified Saturday, April 27, 2013This model illustrates a positive ‘transport’ feedback loop in which lines with different resistance to flows of material result in variation in rates of change in linked entities.
Samambaia Basin - Hydro-ABM
Pedro Phelipe Gonçalves Porto | Published Sunday, April 07, 2019 | Last modified Monday, May 06, 2019This model is a tool to support water management on Samambaia Basin. On it you can explore different scenarios of policy, management and externalities that could influence the water uses. (Scenarios already tested include less rain and payment on water use)
Sensitivity of the Deffuant model to measurement error
Dino Carpentras | Published Monday, June 07, 2021This code can be used to analyze the sensitivity of the Deffuant model to different measurement errors. Specifically to:
- Intrinsic stochastic error
- Binning of the measurement scale
- Random measurement noise
- Psychometric distortions
…
Gini Palma microsimulation
Edgar Oliveira | Published Wednesday, December 11, 2024The model is a microsimulation, where the agents don’t Interact with each other. It simulates income distribution, unemployment dynamics, education, and Family grant in Brazil, focusing on the impact on social inequality. It tracks the indicators Gini index, Lorenz curve, and Palma ratio. The objective is to explore how these factors influence wealth distribution and social inequality over time.
This work was developed in partnership with the Graduate Program in Computational Modeling, in the Universidade Federal do Rio Grande - FURG, in Brazil.
Agent-Based Computational Modeling of Cryptocurrency Design
Felix Ude | Published Friday, June 28, 2019Agent-Based Computational Model of the cryptocurrency Bitcoin with a realistic market and transaction system. Bitcoin’s transaction limit (i.e. block size) and Bitcoin generation can be calibrated and optimized for wealth and network’s hashing power by the Non-Dominated Sorted Genetic Algorithm - II.
Feedback Loop Example: Wildland Fire Spread
James Millington | Published Friday, December 21, 2012 | Last modified Saturday, April 27, 2013This model is a replication of that described by Peterson (2002) and illustrates the ‘spread’ feedback loop type described in Millington (2013).
Displaying 10 of 1188 results for "Ian M Hamilton" clear search