About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 972 results for "M Van Den Hoven" clear search
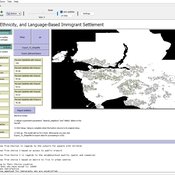
Geospatial Agent-Based Model of Immigrant Settlement Dynamics in Metro Vancouver
Liliana Perez Navid Mahdizadeh Gharakhanlou Maryam Yousefi | Published Wednesday, December 03, 2025This agent-based model simulates how new immigrant households choose where to live in Metro Vancouver under the origins diversity scenario. The model begins with 16,000 household agents, reflecting an expected annual population increase of about 42,500 people based on an average household size of 2.56. Each agent is assigned four characteristics: one of ten origin categories, income level (adjusted using NOC data and recent immigrant earnings), likelihood of having children, and preferred mode of commuting. The ten origin groups are drawn from Census patterns, including six subgroups within the broader Asian category (China, India, the Philippines, Iran, South Korea, and Other Asian countries) and two categories for immigrants from the Americas. This refined classification better captures the diversity of newcomers arriving in the region.
Peer reviewed Strategy with Externalities
J M Applegate Glenn Hoetker | Published Thursday, December 21, 2017The SWE models firms search behaviour as the performance landscape shifts. The shift represents society’s pricing of negative externalities, and the performance landscape is an NK structure. The model is written in NetLogo.
Peer reviewed Empathy & Power
J M Applegate Ned Wellman | Published Monday, November 13, 2017 | Last modified Thursday, December 21, 2017The purpose of this model is to explore the effects of different power structures on a cross-functional team’s prosocial decision making. Are certain power distributions more conducive to the team making prosocial decisions?
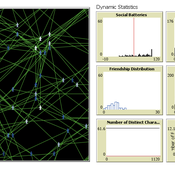
The Friendship Field
Eva Timmer Chrisja van de Kieft | Published Thursday, May 26, 2022 | Last modified Tuesday, August 30, 2022The Friendship Field model aims at modelling friendship formation based on three factors: Extraversion, Resemblance and Status, where social interaction is motivated by the Social Battery. Social Battery is one’s energy and motivation to engage in social contact. Since social contact is crucial for friendship formation, the model included Social Battery to affect social interactions. To our best knowledge, Social Battery is a yet unintroduced concept in research while it is a dynamic factor influencing the social interaction besides one’s characteristics. Extraverts’ Social Batteries charge while interacting and exhaust while being alone. Introverts’ Social Batteries charge while being alone and exhaust while interacting. The aim of the model is to illustrate the concept of Social Battery. Moreover, the Friendship Field shows patterns regarding Extraversion, Resemblance and Status including the mere-exposure effect and friendship by similarity. For the implementation of Status, Kemper’s status-power theory is used. The concept of Social Battery is also linked to Kemper’s theory on the organism as reference group. By running the model for a year (3 interactions moments per day), the friendship dynamics over time can be studied.
We presented the model at the Social Simulation Conference 2022.
CA_Assiut_v1.0
Nina Schwarz Yang Chen m-m-abdelkader Mahmood Abdelkader | Published Sunday, October 09, 2022The purpose of the model is to simulate the future growth of human settlements in the Nile river valley in Egypt. The model contains processes to mimic spatial patterns found in the case study region.
WeDiG Sim
Reza Shamsaee | Published Monday, May 14, 2012 | Last modified Saturday, April 27, 2013WeDiG Sim- Weighted Directed Graph Simulator - is an open source application that serves to simulate complex systems. WeDiG Sim reflects the behaviors of those complex systems that put stress on scale-free, weightedness, and directedness. It has been implemented based on “WeDiG model” that is newly presented in this domain. The WeDiG model can be seen as a generalized version of “Barabási-Albert (BA) model”. WeDiG not only deals with weighed directed systems, but also it can handle the […]
Generic servicising model (SPREE project)
Igor Nikolic Reinier Van Der Veen Kasper H Kisjes | Published Wednesday, August 26, 2015 | Last modified Wednesday, September 28, 2016This generic agent-based model allows the user to simulate and explore the influence of servicising policies on the uptake of servicising and on economic, environmental and social effects, notably absolute decoupling.
MarPEM: An Agent Based Model to Explore the Effects of Policy Instruments on the Transition of the Maritime Fuel System
G Bas I Nikolic K De Boo Am Vaes - Van De Hulsbeek | Published Thursday, June 15, 2017MarPEM is an agent-based model that can be used to study the effects of policy instruments on the transition away from HFO.
Non-attentional visual information transmission in groups under predation
J. Fransje Weerden, van | Published Wednesday, March 25, 2020Our aim is to show effects of group living when only low-level cognition is assumed, such as pattern recognition needed for normal functioning, without assuming individuals have knowledge about others around them or warn them actively.
The model is of a group of vigilant foragers staying within a patch, under attack by a predator. The foragers use attentional scanning for predator detection, and flee after detection. This fleeing action constitutes a visual cue to danger, and can be received non-attentionally by others if it occurs within their limited visual field. The focus of this model is on the effectiveness of this non-attentional visual information reception.
A blind angle obstructing cue reception caused by behaviour can exist in front, morphology causes a blind angle in the back. These limitations are represented by two visual field shapes. The scan for predators is all-around, with distance-dependent detection; reception of flight cues is limited by visual field shape.
Initial parameters for instance: group sizes, movement, vision characteristics for predator detection and for cue reception. Captures (failure), number of times the information reached all individuals at the same time (All-fled, success), and several other effects of the visual settings are recorded.
A simple emulation-based computational model
Carlos M Fernández-Márquez Francisco J Vázquez | Published Tuesday, May 21, 2013 | Last modified Tuesday, February 05, 2019Emulation is one of the simplest and most common mechanisms of social interaction. In this paper we introduce a descriptive computational model that attempts to capture the underlying dynamics of social processes led by emulation.
Displaying 10 of 972 results for "M Van Den Hoven" clear search