About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 204 results network clear search
Agent-based Simulation of Innovation Diffusion
Theresa Elbracht | Published Monday, May 19, 2025The agent-based simulation of innovation diffusion is based on the idea of the Bass model (1969).
The adoption of an agent is driven two parameters: its innovativess p and its prospensity to conform with others. The model is designed for a computational experiment building up on the following four model variations:
(i) the agent population it fully connected and all agents share the same parameter values for p and q
(ii) the agent population it fully connected and agents are heterogeneous, i.e. individual parameter values are drawn from a normal distribution
(iii) the agents population is embeded in a social network and all agents share the same parameter values for p and q
…
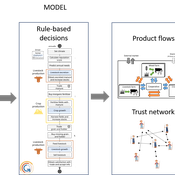
MIXTRUST - crop-livestock interactions at regional level
Myriam Grillot Aurélien Peter | Published Tuesday, February 25, 2025 | Last modified Monday, September 01, 2025The basic idea behind developing MIXTRUST was to represent a network of agricultural stakeholders composed of farmers and a cooperative in a mixed landscape to test its performances in response to risks. A mixed landscape here is a landscape where crop and livestock systems interact by the intermediary of material flows of agricultural products. It can be within mixed farms, or between farms, often specialized, (e.g. straw-manure).
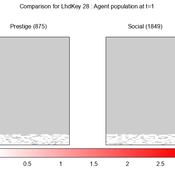
We provide a theory-grounded, socio-geographic agent-based model to present a possible explanation for human movement in the Adriatic region within the Cetina phenomenon.
Focusing on ideas of social capital theory from Piere Bordieu (1986), we implement agent mobility in an abstract geography based on cultural capital (prestige) and social capital (social position). Agents hold myopic representations of social (Schaff, 2016) and geographical networks and decide in a heuristic way on moving (and where) or staying.
The model is implemented in a fork of the Laboratory for Simulation Development (LSD), appended with GIS capabilities (Pereira et. al. 2020).
An Agent-Based Model of Indirect Minority Influence on Social Change
Jiin Jung | Published Wednesday, February 05, 2025This model demonstrates how different psychological mechanisms and network structures generate various patterns of cultural dynamics including cultural diversity, polarization, and majority dominance, as explored by Jung, Bramson, Crano, Page, and Miller (2021). It focuses particularly on the psychological mechanisms of indirect minority influence, a concept introduced by Serge Moscovici (1976, 1980)’s genetic model of social influence, and validates how such influence can lead to social change.
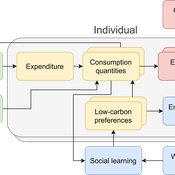
The cultural multiplier of climate policy
Daniel Torren-Peraire | Published Thursday, October 31, 2024For deep decarbonisation, the design of climate policy needs to account for consumption choices being influenced not only by pricing but also by social learning. This involves changes that pertain to the whole spectrum of consumption, possibly involving shifts in lifestyles. In this regard, it is crucial to consider not just short-term social learning processes but also slower, longer-term, cultural change. Against this background, we analyse the interaction between climate policy and cultural change, focusing on carbon taxation. We extend the notion of “social multiplier” of environmental policy derived in an earlier study to the context of multiple consumer needs while allowing for behavioural spillovers between these, giving rise to a “cultural multiplier”. We develop a model to assess how this cultural multiplier contributes to the effectiveness of carbon taxation. Our results show that the cultural multiplier stimulates greater low-carbon consumption compared to fixed preferences. The model results are of particular relevance for policy acceptance due to the cultural multiplier being most effective at low-carbon tax values, relative to a counter-case of short-term social interactions. Notably, at high carbon tax levels, the distinction between social and cultural multiplier effects diminishes, as the strong price signal drives even resistant individuals toward low-carbon consumption. By varying socio-economic conditions, such as substitutability between low- and high-carbon goods, social network structure, proximity of like-minded individuals and the richness of consumption lifestyles, the model provides insight into how cultural change can be leveraged to induce maximum effectiveness of climate policy.
Simple models with different types of complexity
Michael Roos | Published Tuesday, September 17, 2024 | Last modified Saturday, March 01, 2025Hierarchical problem-solving model
The model simulates a hierarchical problem-solving process in which a manager delegates parts of a problem to specialists, who attempt to solve specific aspects based on their unique skills. The goal is to examine how effectively the hierarchical structure works in solving the problem, the total cost of the process, and the resulting solution quality.
Problem-solving random network model
The model simulates a network of agents (generalists) who collaboratively solve a fixed problem by iterating over it and using their individual skills to reduce the problem’s complexity. The goal is to study the dynamics of the problem-solving process, including agent interactions, work cycles, total cost, and solution quality.
GODS: Gossip-Oriented Dilemma Simulator
Jan Majewski | Published Wednesday, September 04, 2024 | Last modified Monday, September 29, 2025Model of influence of access to social information spread via social network on decisions in a two-person game.
Peer reviewed Behavior changes through influence
Daria Soboleva | Published Friday, August 30, 2024The model is designed to simulate the behavior and decision-making processes of individuals (agents) in a social network. It aims to represent the changes in individual probability to take any action based on changes in attributes. The action is anything that can be reasonably influenced by the three influencing methods implemented in this model: peer pressure, social media, and state campaigns, and for which the user has a decision-making model. The model is implemented in the multi-agent programmable environment NetLogo 6.3.0.
Peer reviewed Agent-Based Insight into Eco-Choices: Simulating the Fast Fashion Shift
Daria Soboleva Angel Sánchez | Published Wednesday, August 07, 2024 | Last modified Wednesday, June 11, 2025The present model was created and used for the study titled ``Agent-Based Insight into Eco-Choices: Simulating the Fast Fashion Shift.” The model is implemented in the multi-agent programmable environment NetLogo 6.3.0. The model is designed to simulate the behavior and decision-making processes of individuals (agents) in a social network. It focuses on how agents interact with their peers, social media, and government campaigns, specifically regarding their likelihood to purchase fast fashion.
Agent-Based Model of Transhumant Decision-Making Processes in Senegal
Cheick Amed Diloma Gabriel TRAORE Etienne DELAY Alassane Bah Djibril Diop | Published Wednesday, July 03, 2024Sahelian transhumance is a type of socio-economic and environmental pastoral mobility. It involves the movement of herds from their terroir of origin (i.e., their original pastures) to one or more host terroirs, followed by a return to the terroir of origin. According to certain pastoralists, the mobility of herds is planned to prevent environmental degradation, given the continuous dependence of these herds on their environment. However, these herds emit Greenhouse Gases (GHGs) in the spaces they traverse. Given that GHGs contribute to global warming, our long-term objective is to quantify the GHGs emitted by Sahelian herds. The determination of these herds’ GHG emissions requires: (1) the artificial replication of the transhumance, and (2) precise knowledge of the space used during their transhumance.
This article presents the design of an artificial replication of the transhumance through an agent-based model named MSTRANS. MSTRANS determines the space used by transhumant herds, based on the decision-making process of Sahelian transhumants.
MSTRANS integrates a constrained multi-objective optimization problem and algorithms into an agent-based model. The constrained multi-objective optimization problem encapsulates the rationality and adaptability of pastoral strategies. Interactions between a transhumant and its socio-economic network are modeled using algorithms, diffusion processes, and within the multi-objective optimization problem. The dynamics of pastoral resources are formalized at various spatio-temporal scales using equations that are integrated into the algorithms.
The results of MSTRANS are validated using GPS data collected from transhumant herds in Senegal. MSTRANS results highlight the relevance of integrated models and constrained multi-objective optimization for modeling and monitoring the movements of transhumant herds in the Sahel. Now specialists in calculating greenhouse gas emissions have a reproducible and reusable tool for determining the space occupied by transhumant herds in a Sahelian country. In addition, decision-makers, pastoralists, veterinarians and traders have a reproducible and reusable tool to help them make environmental and socio-economic decisions.
Displaying 10 of 204 results network clear search