About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 988 results for "Rolf Anker Ims" clear search
Evolutionary Model of Subculture Choice
Diogo Alves | Published Monday, December 19, 2022This is an original model of (sub)culture diffusion.
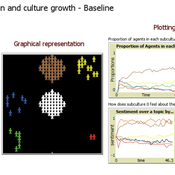
It features a set of agents (dubbed “partygoers”) organized initially in clusters, having properties such as age and a chromosome of opinions about 6 different topics. The partygoers interact with a set of cultures (also having a set of opinions subsuming those of its members), in the sense of refractory or unhappy members of each setting about to find a new culture and trading information encoded in the genetic string (originally encoded as -1, 0, and 1, resp. a negative, neutral, and positive opinion about each of the 6 traits/aspects, e.g. the use of recreational drugs). There are 5 subcultures that both influence (through the aforementioned genetic operations of mutation and recombination of chromosomes simulating exchange of opinions) and are influenced by its members (since a group is a weighted average of the opinions and actions of its constituents). The objective of this feedback loop is to investigate under which conditions certain subculture sizes emerge, but the model is open to many other kinds of explorations as well.
Resisting hostility
Sylvie Huet | Published Thursday, December 20, 2018We propose an agent-based model leading to a decrease or an increase of hostility between agents after a major cultural threat such as a terrorist attack. The model is inspired from the Terror Management Theory and the Social Judgement Theory. An agent has a cultural identity defined through its acceptance segments about each of three different cultural worldviews (i.e., Atheist, Muslim, Christian) of the considered society. An agent’s acceptance segment is composed from its acceptable positions toward a cultural worldview, including its most acceptable position. An agent forms an attitude about another agent depending on the similarity between their cultural identities. When a terrorist attack is perpetrated in the name of an extreme cultural identity, the negatively perceived agents from this extreme cultural identity point of view tend to decrease the width of their acceptance segments in order to differentiate themselves more from the threatening cultural identity
An agent-based model of adaptive cycles of the spruce budworm
Julia Schindler | Published Saturday, August 18, 2012 | Last modified Saturday, April 27, 2013This is an empirically calibrated agent-based model that replicates spruce-budworm outbreaks, one of the most cited adaptive cycles reported. The adaptive-cycle metaphor by L. H. Gunderson and C. S. Holling posits the cross-case existence of repeating cycles of growth, conservation, collapse, and renewal in many complex systems, triggered by loss of resilience. This model is one of the first agent-based models of such cycles, with the novelty that adaptive cycles are not defined by system- […]
Agent-based Simulation of Innovation Diffusion
Theresa Elbracht | Published Monday, May 19, 2025The agent-based simulation of innovation diffusion is based on the idea of the Bass model (1969).
The adoption of an agent is driven two parameters: its innovativess p and its prospensity to conform with others. The model is designed for a computational experiment building up on the following four model variations:
(i) the agent population it fully connected and all agents share the same parameter values for p and q
(ii) the agent population it fully connected and agents are heterogeneous, i.e. individual parameter values are drawn from a normal distribution
(iii) the agents population is embeded in a social network and all agents share the same parameter values for p and q
…
A simplified Arthur & Polak logic circuit model of combinatory technology build-out via incremental development. Only some inventions trigger radical effects, suggesting they depend on whole interdependent systems rather than specific innovations.
Peer reviewed Strategy with Externalities
J M Applegate Glenn Hoetker | Published Thursday, December 21, 2017The SWE models firms search behaviour as the performance landscape shifts. The shift represents society’s pricing of negative externalities, and the performance landscape is an NK structure. The model is written in NetLogo.
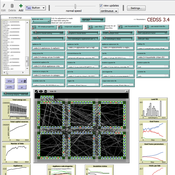
CEDSS is an agent-based model of domestic energy demand at the level of a small community.
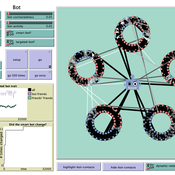
How do bots influence beliefs on social media? Why do beliefs propagated by social bots spread far and wide, yet does their direct influence appear to be limited?
This model extends Axelrod’s model for the dissemination of culture (1997), with a social bot agent–an agent who only sends information and cannot be influenced themselves. The basic network is a ring network with N agents connected to k nearest neighbors. The agents have a cultural profile with F features and Q traits per feature. When two agents interact, the sending agent sends the trait of a randomly chosen feature to the receiving agent, who adopts this trait with a probability equal to their similarity. To this network, we add a bot agents who is given a unique trait on the first feature and is connected to a proportion of the agents in the model equal to ‘bot-connectedness’. At each timestep, the bot is chosen to spread one of its traits to its neighbors with a probility equal to ‘bot-activity’.
The main finding in this model is that, generally, bot activity and bot connectedness are both negatively related to the success of the bot in spreading its unique message, in equilibrium. The mechanism is that very active and well connected bots quickly influence their direct contacts, who then grow too dissimilar from the bot’s indirect contacts to quickly, preventing indirect influence. A less active and less connected bot leaves more space for indirect influence to occur, and is therefore more successful in the long run.
We propose here a computational model of school segregation that is aligned with a corresponding Schelling-type model of residential segregation. To adapt the model for application to school segregation, we move beyond previous work by combining two preference arguments in modeling parents’ school choice, preferences for the ethnic composition of a school and preferences for minimizing the travelling distance to the school.
ThomondSim
Vinicius Marino Carvalho | Published Monday, April 25, 2022 | Last modified Friday, May 12, 2023ThomondSim is a simulation of the political and economic landscape of the medieval kingdom of Thomond, southwestern Ireland, between 1276 and 1318.
Its goal is to analyze how deteriorating environmental and economic conditions caused by the Little Ice Age (LIA), the Great European Famine of 1315-1322, and wars between England and Scotland affected the outcomes of a local war involving Gaelic and English aristocratic lineages.
This ABM attempts to model both the effects of devastation on the human environment and the modus operandi of late-medieval war and diplomacy.
The model is the digital counterpart of the science discovery board game The Triumphs of Turlough. Its procedures closely correspond to the game’s mechanics, to the point that ToT can be considered an interactive, analog version of this ABM.
Displaying 10 of 988 results for "Rolf Anker Ims" clear search