About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 286 results for "Ned Wellman" clear search
Artificial Long House Valley-Black Mesa
Lisa Sattenspiel Amy Warren | Published Thursday, March 19, 2020This model is an extension of the Artificial Long House Valley (ALHV) model developed by the authors (Swedlund et al. 2016; Warren and Sattenspiel 2020). The ALHV model simulates the population dynamics of individuals within the Long House Valley of Arizona from AD 800 to 1350. Individuals are aggregated into households that participate in annual agricultural and demographic cycles. The present version of the model incorporates features of the ALHV model including realistic age-specific fertility and mortality and, in addition, it adds the Black Mesa environment and population, as well as additional methods to allow migration between the two regions.
As is the case for previous versions of the ALHV model as well as the Artificial Anasazi (AA) model from which the ALHV model was derived (Axtell et al. 2002; Janssen 2009), this version makes use of detailed archaeological and paleoenvironmental data from the Long House Valley and the adjacent areas in Arizona. It also uses the same methods as the original AA model to estimate annual maize productivity of various agricultural zones within the Long House Valley. A new environment and associated methods have been developed for Black Mesa. Productivity estimates from both regions are used to determine suitable locations for households and farms during each year of the simulation.
Peer reviewed Evolution of Cooperation in Asymmetric Commons Dilemmas
Marco Janssen Nathan Rollins | Published Friday, August 20, 2010 | Last modified Saturday, April 27, 2013This model can be used to explore under which conditions agents behave as observed in field experiments on irrigation games.
Linear Threshold
Kaushik Sarkar | Published Saturday, November 03, 2012 | Last modified Saturday, April 27, 2013NetLogo implementation of Linear Threshold model of influence propagation.
Will it spread or not? The effects of social influences and network topology on innovation diffusion
Sebastiano Delre | Published Monday, October 24, 2011 | Last modified Saturday, April 27, 2013This models simulates innovation diffusion curves and it tests the effects of the degree and the direction of social influences. This model replicates, extends and departs from classical percolation models.
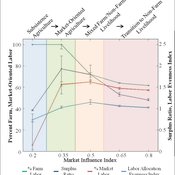
Land-Livelihood Transitions
Nicholas Magliocca Daniel G Brown Erle C Ellis | Published Monday, September 09, 2013 | Last modified Friday, September 13, 2013Implemented as a virtual laboratory, this model explores transitions in land-use and livelihood decisions that emerge from changing local and global conditions.
This is a social trust model for investigating the social relationships and social networks in the real world and in social media.
A model to explore the link between the gender-gap reversal in education and relative divorce risks
Jan Van Bavel Christine Schnor André Grow | Published Thursday, June 30, 2016 | Last modified Wednesday, September 13, 2017This model explores a social mechanism that links the reversal of the gender gap in education with changing patterns in relative divorce risks in 12 European countries.
Multi Asset Variable Network Stock Market Model
Matthew Oldham | Published Monday, September 12, 2016 | Last modified Tuesday, October 10, 2017An artifcal stock market model that allows users to vary the number of risky assets as well as the network topology that investors forms in an attempt to understand the dynamics of the market.
Potato late blight model
Francine Pacilly | Published Friday, April 13, 2018The purpose of the model is to simulate the spatial dynamics of potato late blight to analyse whether resistant varieties can be used effectively for sustainable disease control. The model represents an agricultural landscape with potato fields and data of a Dutch agricultural region is used as input for the model. We simulated potato production, disease spread and pathogen evolution during the growing season (April to September) for 36 years. Since late blight development and crop growth is weather dependent, measured weather data is used as model input. A susceptible and late blight resistant potato variety are distinguished. The resistant variety has a potentially lower yield but cannot get infected with the disease. However, during the growing season virulent spores can emerge as a result of mutations during spore production. This new virulent strain is able to infect the resistant fields, resulting in resistance breakdown. The model shows how disease severity, resistance durability and potato yield are affected by the fraction of fields across a landscape with a disease-resistant potato variety.
Agent-Based Model of Social Care with Kinship Networks
Umberto Gostoli Eric Silverman | Published Thursday, October 14, 2021The purpose of this model is the simulation of social care provision in the UK, in which individual agents can decide to provide informal care, or pay for private care, for their loved ones. Agents base these decisions on factors including their own health, employment status, financial resources, relationship to the individual in need and geographical location. The model simulates care provision as a negotiation process conducted between agents across their kinship networks, with agents with stronger familial relationships to the recipient being more likely to attempt to allocate time to care provision. The model also simulates demographic change, the impact of socioeconomic status, and allows agents to relocate and change jobs or reduce working hours in order to provide care.
Despite the relative lack of empirical data in this model, the model is able to reproduce plausible patterns of social care provision. The inclusion of detailed economic and behavioural mechanisms allows this model to serve as a useful policy development tool; complex behavioural interventions can be implemented in simulation and tested on a virtual population before applying them in real-world contexts.
Displaying 10 of 286 results for "Ned Wellman" clear search